Quad9 Cybersecurity Trends and Insights | April 2023
A Monthly Insight into Quad9’s Top Blocks
In December 2022, Quad9 published our first monthly, in-depth report exploring the trending DNS lookups of malicious hostnames we blocked the prior month. Each month, Quad9 users can download the entire report, which will provide a breakdown of several cybersecurity metrics, including but not limited to the prior month’s highest trending malware by volume of attempted domain access and type.
This information is valuable because it further sheds light on the most prominent malware, phishing, spyware, and botnet threats of which individuals and network administrators should be aware. For Quad9 users, the information in the monthly reports is more than supplemental intel surrounding trending cybersecurity and privacy threats. It also serves as additional peace of mind that Quad9’s public and free DNS service is helping to provide its users with a safer, more private online experience.
Quad9 Identified Cybersecurity Threat Trends – March 2023 Data
Last month, Quad9 observed a diverse array of threat categories. Among the many types of threats blocked and analyzed, the top three were malvertising, DDoS, and banking trojans. The graphic below represents Quad9’s identified malware trends by threat category during March 2023 — all of which were blocked by Quad9.
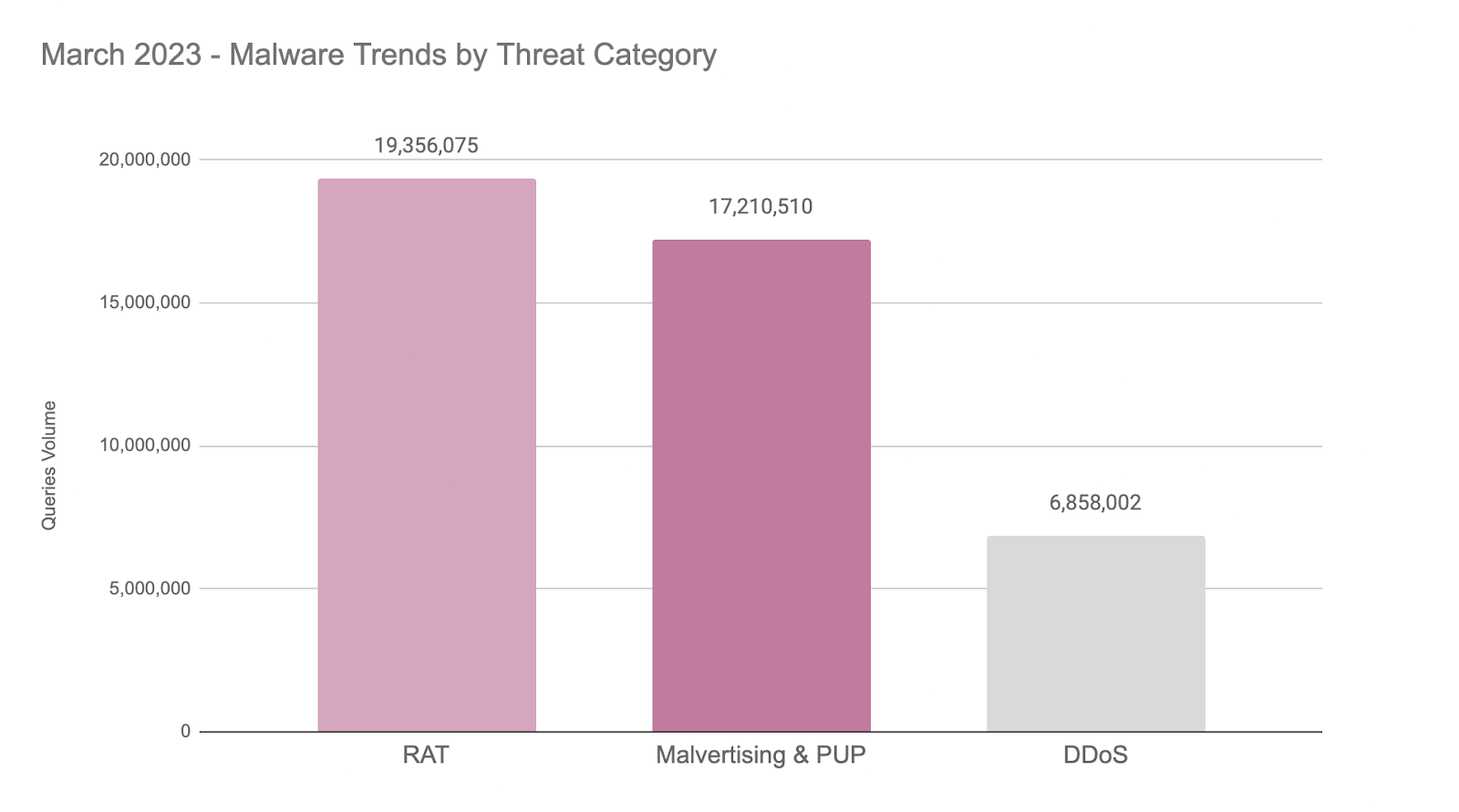
The graph above represents malware trends observed and blocked by Quad9 during March 2023. Due to the volume of DNS requests, Quad9 does not collect all the DNS requests. Thus, analyzed samples were recorded daily for 60 seconds each hour. It should be noted that Quad9’s methodology was changed this month to improve data quality. Source: quad9.net
During March 2023, malvertising and potentially unwanted programs (PUPs) continued to be one of the most frequently identified and blocked threats. Observations of this threat type have become increasingly common in recent months. According to the Center for Internet Security, malvertising is the practice of injecting malicious code in otherwise legitimate ads distributed across advertising networks. Once an infected ad — which is exceptionally difficult for advertising networks to identify — is displayed on partner websites, users of that website become vulnerable to the malicious code embedded in the ad. An infected user’s machine typically connects to a server hosting various exploit kits. Once executed, these exploit kits attempt to identify vulnerabilities on the user’s machine. These exploit kits are often associated with malware that can grant admin access to an infected machine, mine for sensitive data, execute ransomware, or connect the user’s machine to a botnet. [Source].
Among the observed and blocked user queries to malvertising networks and domains attributed to PUPs, the Omnatuor Malvertising Network remained the most prevalent during March 2023. All the top blocked domains belonging to the Omnatour network were hosted on the IP range 139.45.192.0/19, which belongs to AS9002-RETN-AS GB.
In addition to the Omnatuor Malvertising Network, observations and blocks to the 62.122.171.6 Malvertising Network and Wave Browser were also notable during March 2023. The 62.122.171.6 Malvertising Network is a rising threat hosted on the IP address 62.122.171.6 belonging to AS50245 – SERVEREL-AS, which was located in the US at the time of our research. Wave Browser is a PUP that installs what appears to the user as Google Chrome. However, Wave Browser is designed to display unwanted ads. Even though Wave Browser is not technically a virus or malware, it does make a user’s computer vulnerable to malicious software. Additionally, Wave Browser tracks users’ data, making it accessible to cyber criminals, , and can make unauthorized changes on users’ computers.
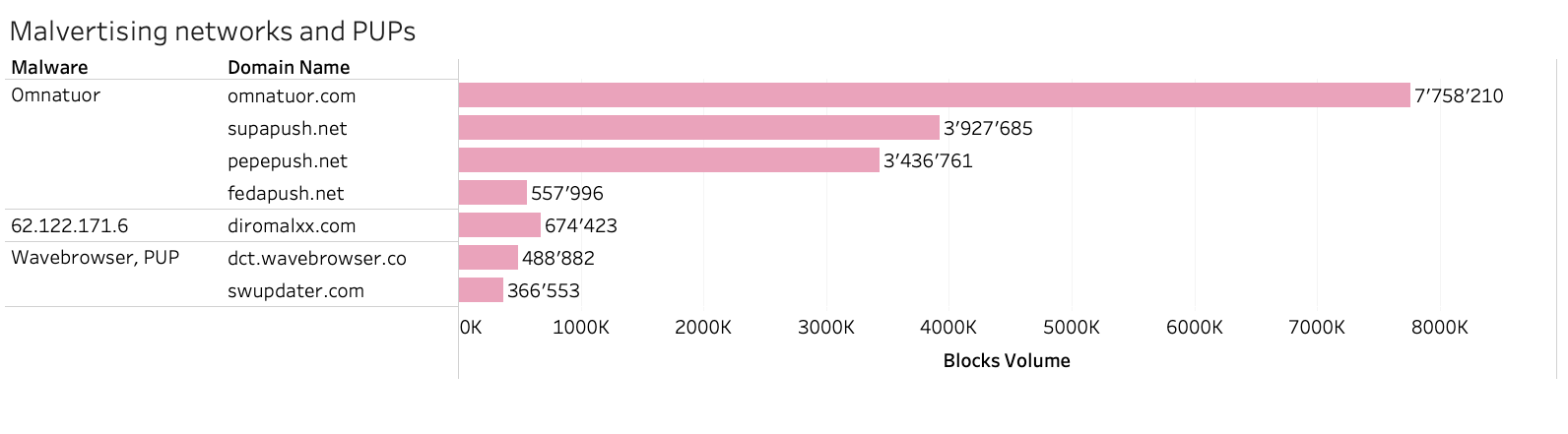
Source: quad9.net March 2023 - Malvertising networks and PUPs
Like February 2023, we observed a lower volume of queries to domains attributed to DDoS threats during March 2023. The domain which recorded the highest volume of DDoS traffic continued to be attributed to Fodcha Command and Control (C2) server. Fodcha Command remains a relatively new yet powerful DDoS botnet, discovered by 360 Netlab researchers in April 2022. This DDoS botnet has caused quite a stir within the cybersecurity community, as researchers report the latest version has grown to an unprecedented scale. Furthermore, Quad9’s data suggests that attackers will still be interested in supply chain vulnerabilities, which are difficult for users to identify and remediate.
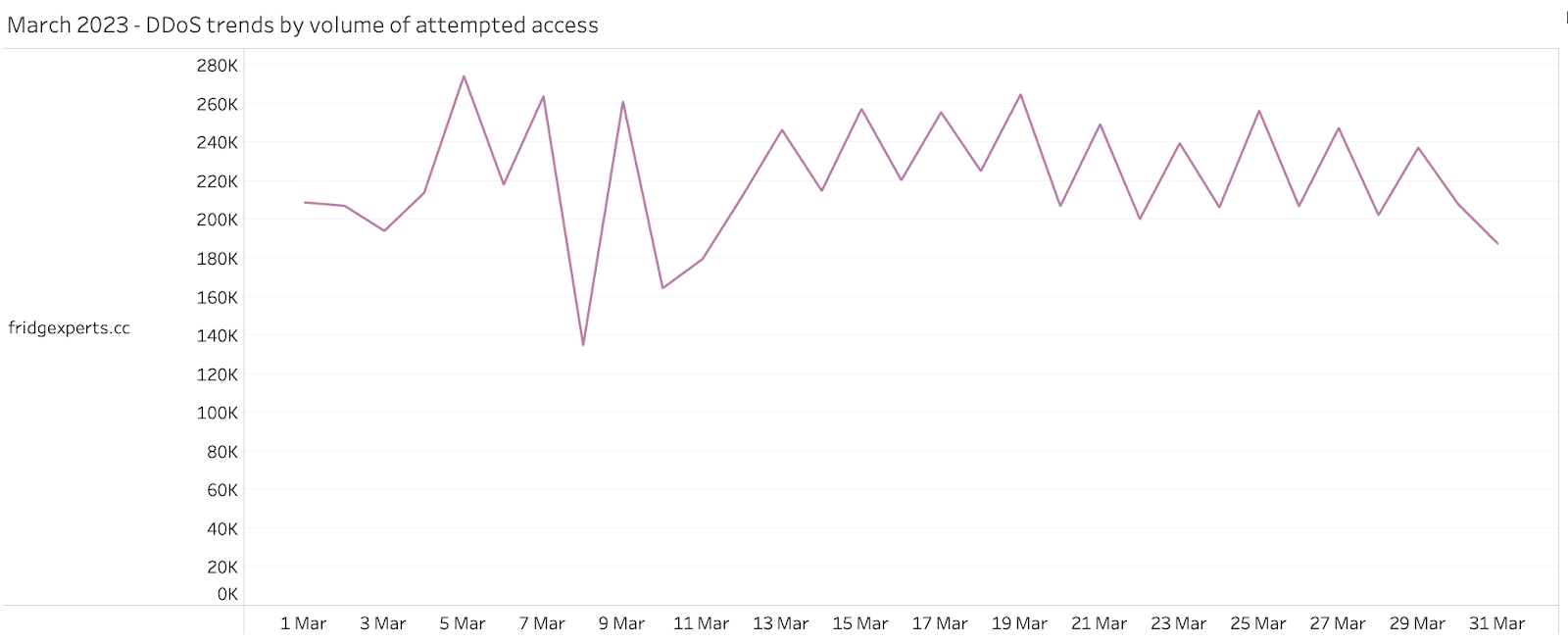
Source: quad9.net March 2023 - DDoS trends
The final observed threat we would like to discuss is the JavaScript threat, ViperSoftX. This multi-stage cryptocurrency stealer is distributed through torrents and file-sharing sites. ViperSoftX was initially observed in 2020 and has grown extensively. Based on Quad9’s observations, this threat has recently been actively exploited. ViperSoftX is a Windows malware deployed via a Google Chrome extension named “VenomSoftX”. Quad9 observed multiple domains generated using a domain generation algorithm (DGA) reported by threat researchers. [Source]
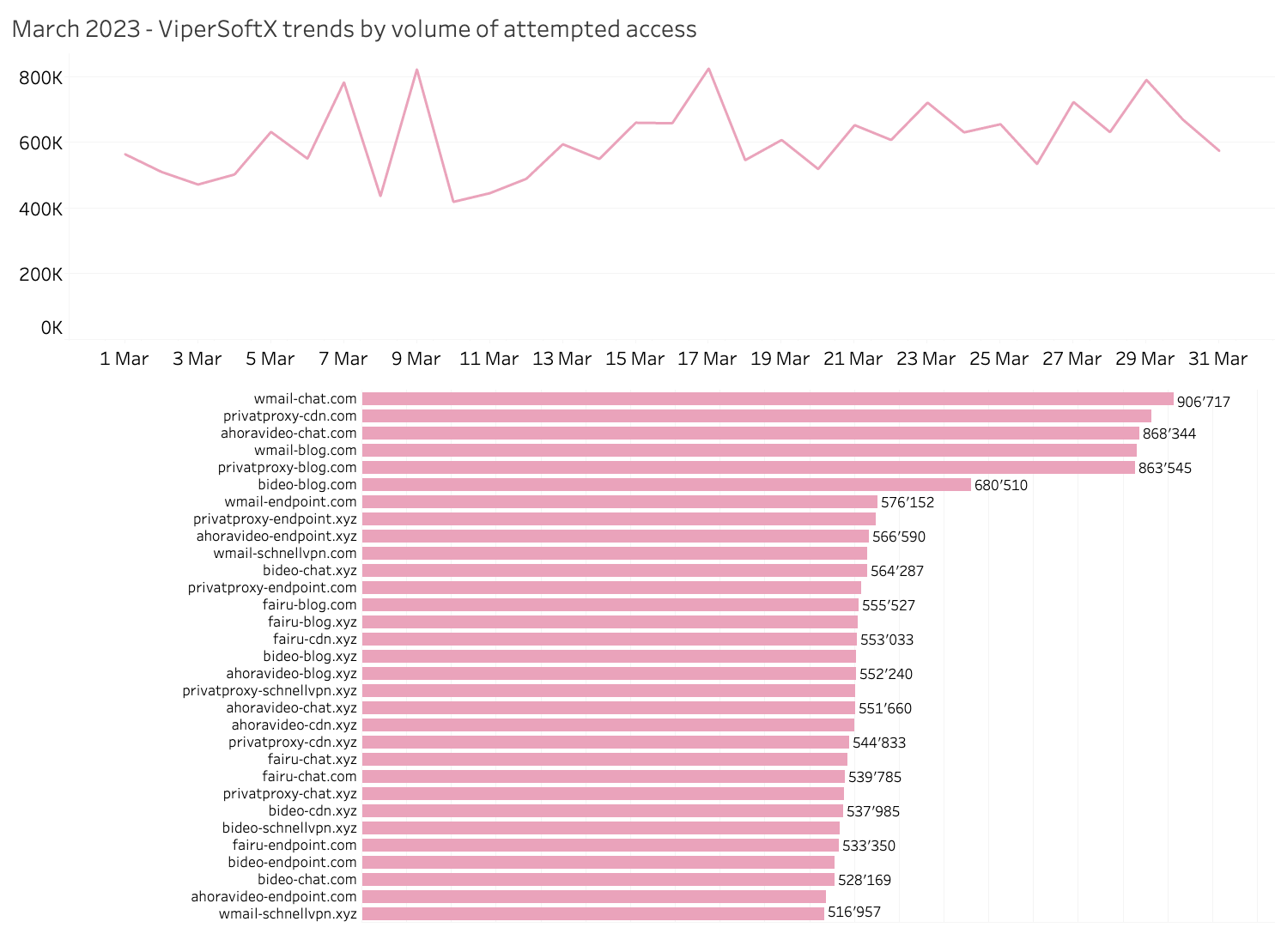
Source: quad9.net March 2023 - ViperSoftX trends by volume of attempted access
The Takeaway
Quad9’s mission is to improve the security and stability of the internet, creating an ecosystem where users are less vulnerable to risks and more effective in their daily online interactions. By preventing connections to known malicious sites, Quad9 reduces exposure risks before they are downloaded to a device or before potential victims gain access to fraudulent websites.
Access the full April 2023 report report
About Quad9
Quad9, a nonprofit in the US and Switzerland, provides free cybersecurity services to the emerging world via secure and private DNS lookup. Quad9 currently operates over 200 locations across more than 90 nations, blocking hundreds of millions of malware, phishing, and spyware events daily for millions of end users. Quad9 reduces harm in vulnerable regions, increases privacy against criminal or institutionalized interception of Internet data, and improves performance in under-served areas. Quad9 is a collaboration with Packet Clearing House (PCH), Global Cyber Alliance, and IBM.
References:
1.https://www.cisecurity.org/insights/blog/malvertising#:~:text=Malvertising%2C%20or%20malicious%20advertising%2C%20is,or%20malicious%20code%20into%20ads
2. https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory/vast-malvertising-network-hijacks-browser-settings-to-spread-riskware/
3. https://urlscan.io/ip/139.45.197.253
4. https://urlscan.io/search/#page.ip:%2262.122.171.6%22
5. https://www.technewstoday.com/wave-browser/
6. https://www.bleepingcomputer.com/news/security/fodcha-ddos-botnet-reaches-1tbps-in-power-injects-ransoms-in-packets/
7. https://chris.partridge.tech/2022/evolution-of-vipersoftx-dga


