Quad9 Cybersecurity Trends and Insights March 2023
A Monthly Insight into Quad9’s Top Blocks
In December 2022, Quad9 published our first monthly, in-depth report exploring the trending DNS lookups of malicious hostnames we blocked the prior month. Each month, Quad9 users can download the entire report, which will provide a breakdown of several cybersecurity metrics, including but not limited to the prior month’s highest trending malware by volume of attempted domain access and type.
This information is valuable because it further sheds light on the most prominent malware, phishing, spyware, and botnet threats of which individuals and network administrators should be aware. For Quad9 users, the information in the monthly reports is more than supplemental intel surrounding trending cybersecurity and privacy threats. They also serve as additional peace of mind that Quad9’s public and free DNS service is helping to provide its users with a safer, more private online experience.
Quad9 Identified Cybersecurity Threat Trends – February 2023 Data
Last month, Quad9 observed a diverse array of threat categories. Among the many types of threats blocked and analyzed, the top three were malvertising, DDoS, and banking trojans. The graphic below represents Quad9’s identified malware trends by threat category during February 2023 — all of which were blocked by Quad9.
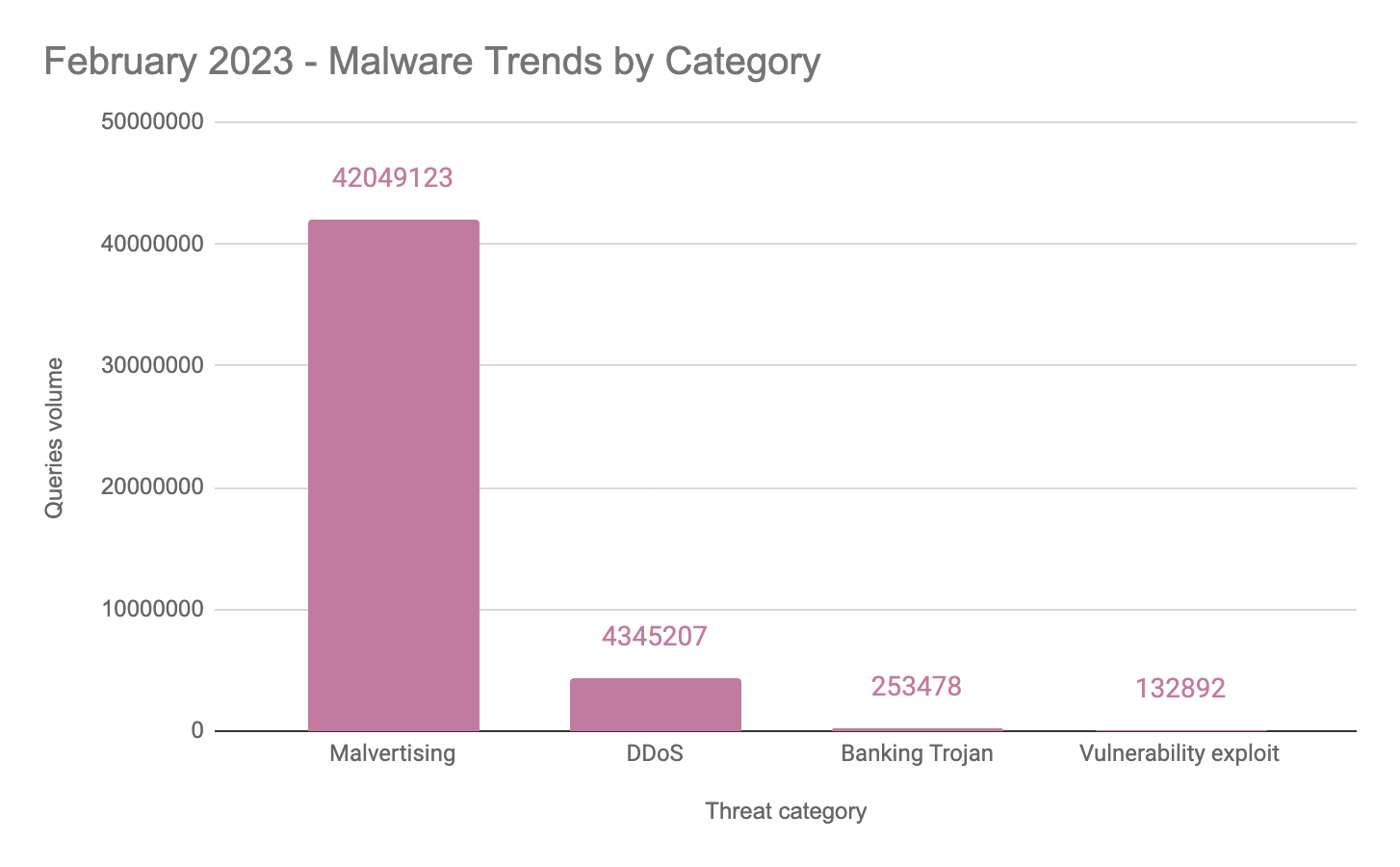
The graph above represents malware trends observed and blocked by Quad9 during February 2023. Due to the volume of DNS requests, Quad9 does not collect all the DNS requests; thus, analyzed samples were recorded daily for 60 seconds each hour. Note: Quad9’s methodology changed this month to improve data quality. Source: quad9.net
During February 2023, the threat type with the highest volume of observations for blocks was malvertising. Measurements of this threat type have become increasingly common in recent months. According to the Center for Internet Security, malvertising is the practice of injecting malicious code in otherwise legitimate ads which are then distributed across advertising networks. Once an infected ad — which is exceptionally difficult for advertising networks to identify — is displayed on a partner website, users become vulnerable to the malicious code embedded in the ad. An infected user’s machine typically connects to a server hosting various exploit kits. Once executed, these exploit kits attempt to identify vulnerabilities on the user’s device. These exploit kits are often associated with malware that can grant admin access to an infected machine, mine for sensitive data, execute ransomware, or connect the user’s machine to a botnet. [Source].
The Omnatuor Malvertising Network was most prevalent during February 2023 among the observed and blocked domains associated with malvertising. The IP range 139.45.192.0/19 belongs to AS9002 - RETN-AS, GB and hosts all of the top blocked domains belonging to the Omnatour. During February 2023, Quad9 recorded 41.4 million blocked queries to this malvertising network and only identified four domains belonging to Omnatour Malvertising Network.
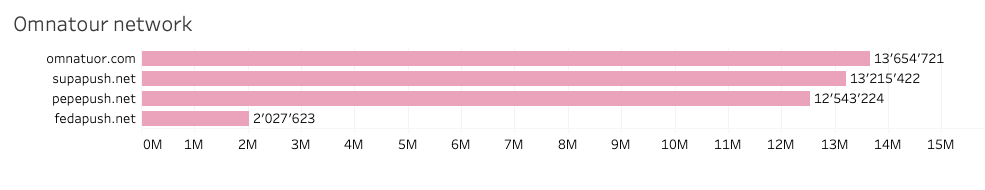
Source: quad9.net
The Omnatuor malvertising campaign targets and compromises vulnerable WordPress websites through embedded malicious JavaScript or PHP code. Once in place, the code redirects users to view and click malvertisements through pop-ups and push notifications. [Source]
During February 2023, Quad9 also observed and blocked another malvertising threat that is on the rise — the 62.122.171.6 Malvertising Network. At the time of our research, this malvertising network, which is hosted on the IP 62.122.171.6, belongs to US-based AS50245 – SEVEREL-AS [Source]. Quad9 identified eight domains for this malvertising network among the top blocked domains.
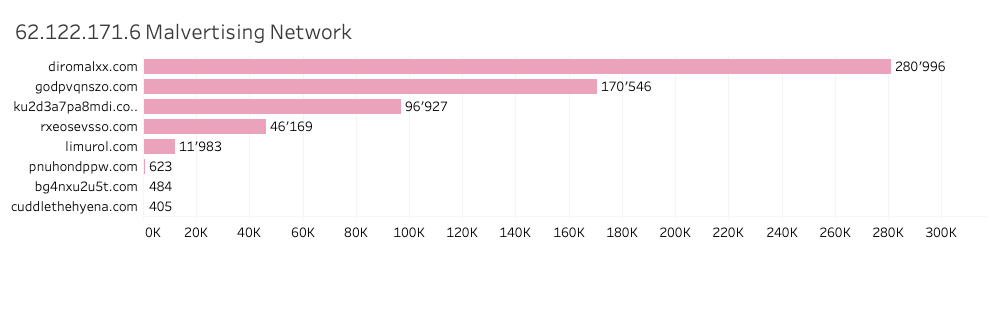
Source: quad9.net
Domains attributed to DDoS threats were the second-highest volume threat type observed and blocked by Quad9 during February 2023. In contrast to previous months, Quad9 observed a lower volume of queries to domains associated with DDoS attack vectors.
The domain which recorded the highest volume of DDoS traffic was attributed to Fodcha Command and Control (C2) server. Fodcha Command remains a relatively new, yet powerful DDoS botnet, discovered by 360 Netlab researchers in April 2022. This DDoS botnet has caused quite a stir within the cybersecurity community, as researchers report the latest version having grown to an unprecedented scale. Furthermore, Quad9’s data suggests that attackers will still be interested in supply chain vulnerabilities, which are difficult for users to identify and remediate.
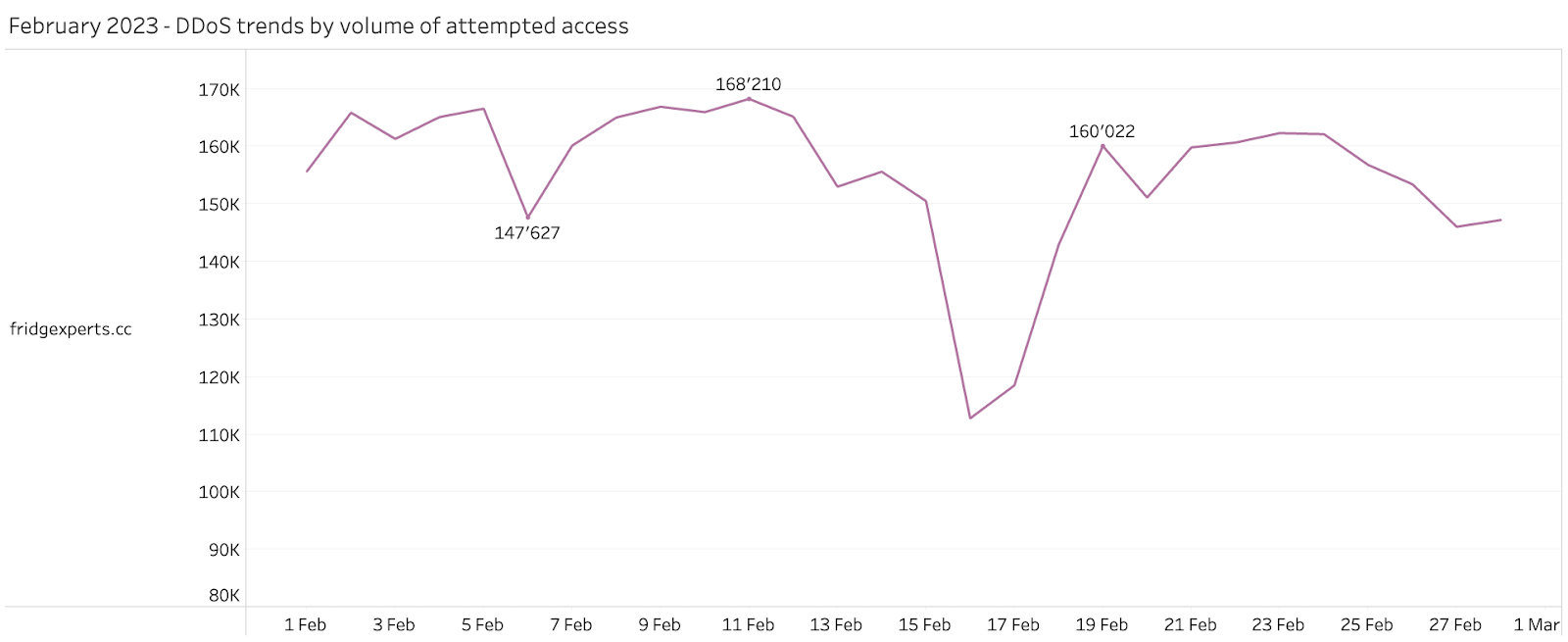
Source: quad9.net
Gozi (Ursnif) Campaign - Quad9 first observed queries to the domain attributed to the Gozi campaign in December 2022. Initial data showed the campaign was active for several days before subsiding. However, throughout February 2023, Quad9 observed many attempts to access weiqeqwens[.]com — a domain attributed to Gozi’s campaign. Gozi (also known as Ursnif) is a banking trojan that is spread through malspam with a Microsoft Office document attachment or ZIP file. Ursnif is designed to collect victim information from cookies, login pages, and web forms.
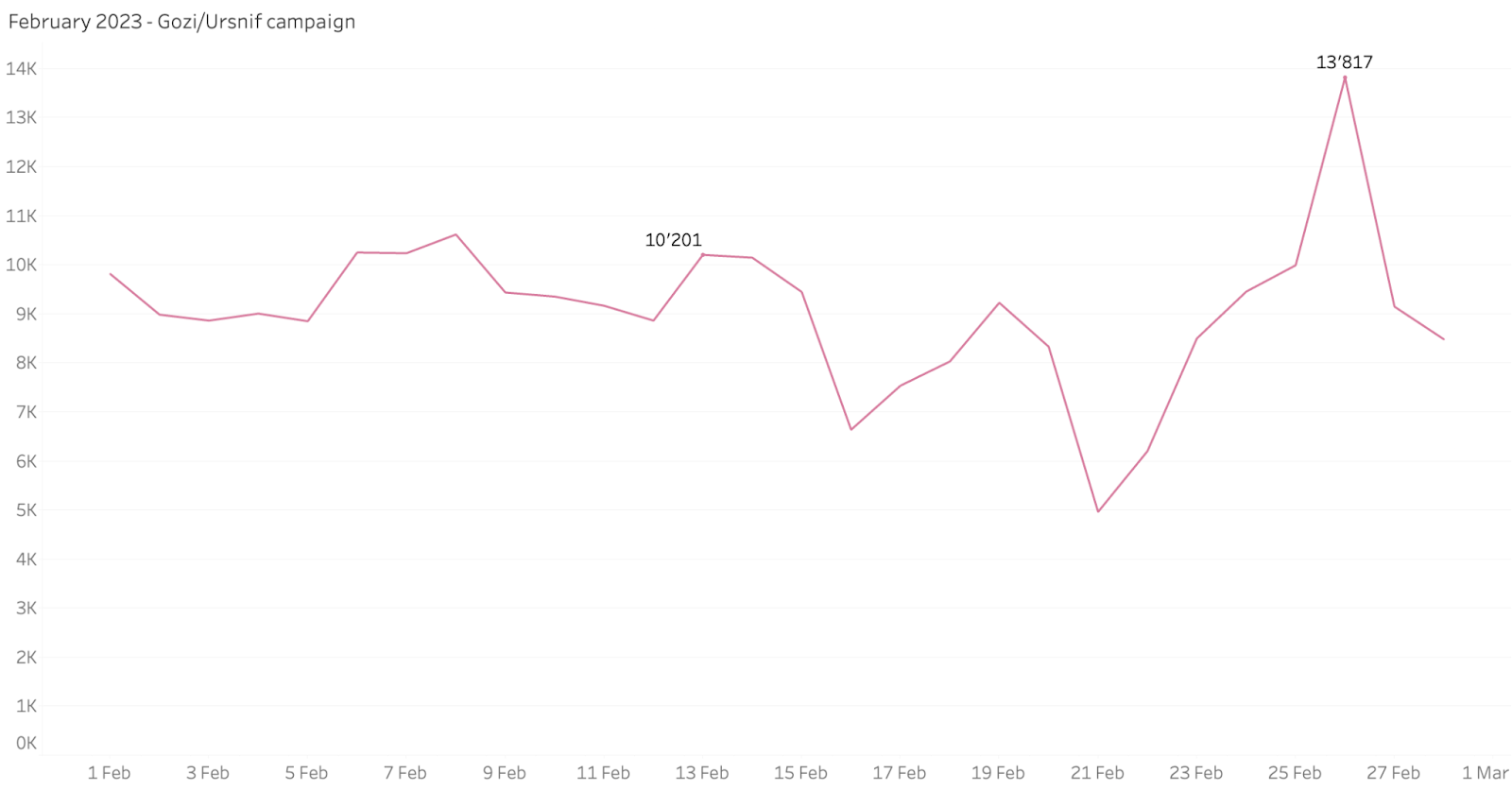
Source: quad9.net
APT37 - The last notable active campaign observed by Quad9 during February 2023 was the APT37 campaign, which leverages Internet Explorer 0-day to target users. APT37 distributes Word documents disguised as normal Microsoft Office URLs. APT37 is a North Korean state-sponsored cyber espionage group targeting victims primarily in South Korea. In the most recent campaign — though not for the first time — Threat Actors have used Internet Explorer 0-day exploits to target victims. The abused 0-day vulnerability is in the Jscript engine of Internet Explorer [Source]. Additionally, it should be noted that the URL used in the fake Word document (ms-offices[.]com) is becoming very cleverly disguised to closely resemble the normal URL. When this report was written, researchers could not determine the final payload of the campaign.
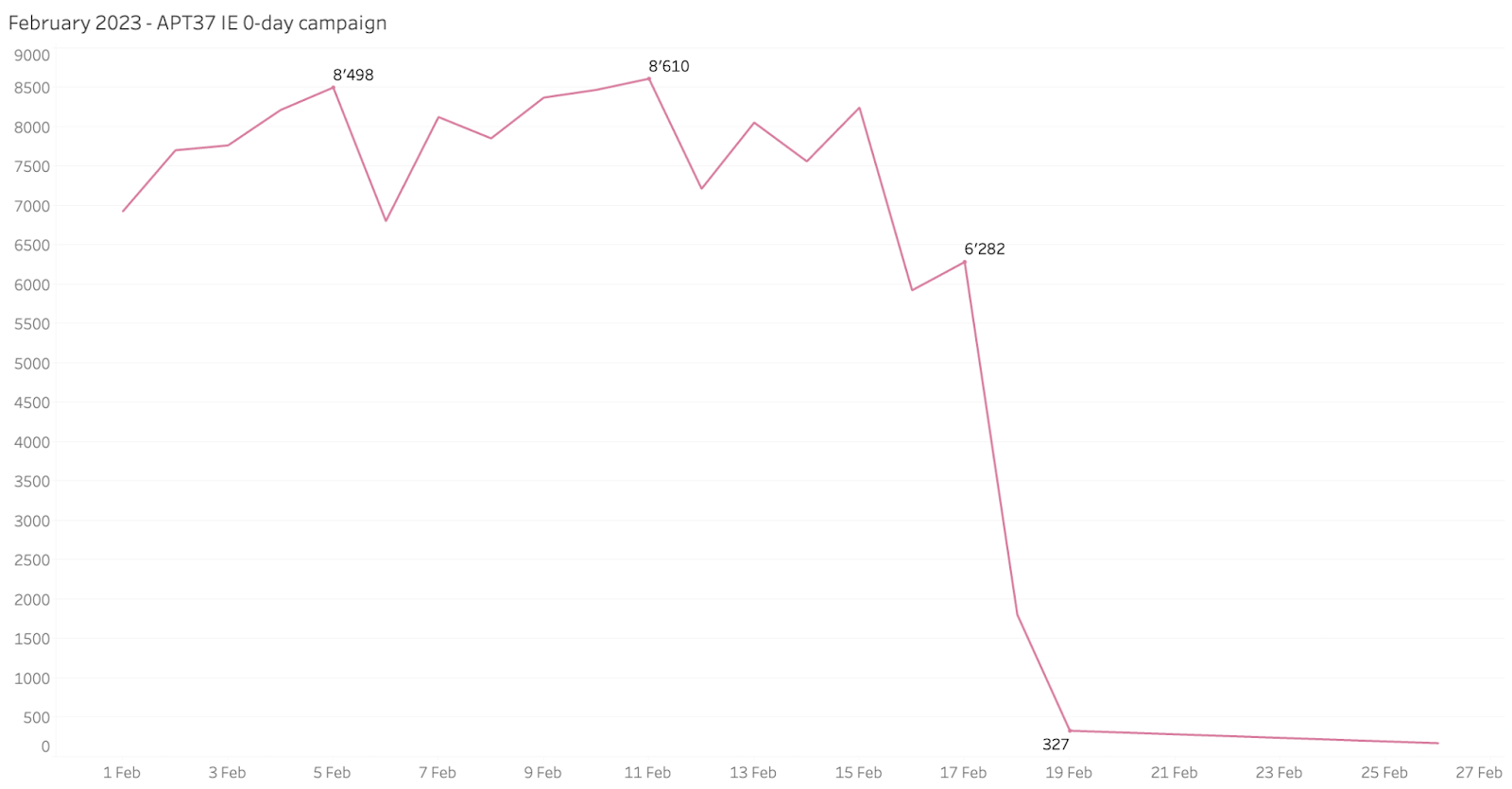
Source: quad9.net
The Takeaway
Quad9’s mission is to improve the security and stability of the internet, creating an ecosystem where users are less vulnerable to risks and more effective in their daily online interactions. By preventing connections to known malicious sites, Quad9 reduces exposure risks before they are downloaded to a device or before potential victims gain access to fraudulent websites.
Access the entire March 2023 report.
About Quad9
Quad9, a nonprofit in the US and Switzerland, provides free cybersecurity services to the emerging world via secure and private DNS lookup. Quad9 currently operates over 200 locations across more than 90 nations, blocking hundreds of millions of malware, phishing, and spyware events daily for millions of end users. Quad9 reduces harm in vulnerable regions, increases privacy against criminal or institutionalized interception of Internet data, and improves performance in under-served areas. Quad9 is a collaboration with Packet Clearing House (PCH), Global Cyber Alliance, and IBM.
References:
3. https://urlscan.io/ip/139.45.197.253


